This article appears in the Spring 2017 digital issue of DOCUMENT Strategy. Subscribe.
Image by: kotoffei, ©2017 Getty Images
Cybersecurity is a strategic priority for most organizations. With recent high-profile breach incidents, including Home Depot, Target, and Sony, many companies are asking themselves, “Will I be next?” The answer is “yes,” based on the number of widespread and increasingly advanced attacks. Some of these data breaches are not only a result of internal malicious acts but also unintentional mistakes by employees.
Ultimately, the chief information security officer (CISO) needs to understand the information footprint across systems, determine the value/risk of loss, and protect against cyberattacks through the deployment of control activities, which are commensurate with the value/risk of these information systems. For the last several years, CISOs have focused almost exclusively on protecting the perimeter (even going as far as to use endpoint protection). If most agree that they will likely experience a data breach, then this attention to the perimeter only addresses a portion of the risk.
We’ve all heard for years that information technology (IT) and cybersecurity require people, process, and technology; however, over the years, “people” and “process” have not received the same attention as “technology.” Cybersecurity in many organizations has been regarded as a technical problem, handled by technical people and buried in IT. With the widespread use of mobile computing and the explosive growth of Internet of things (IoT) devices (growing from 6.4 billion connected devices to over 50 billion by 2020), a focus on people and process must move up in prominence to mount a coordinated defense and, eventually, an offense.
©2017 DOCUMENT Strategy Media
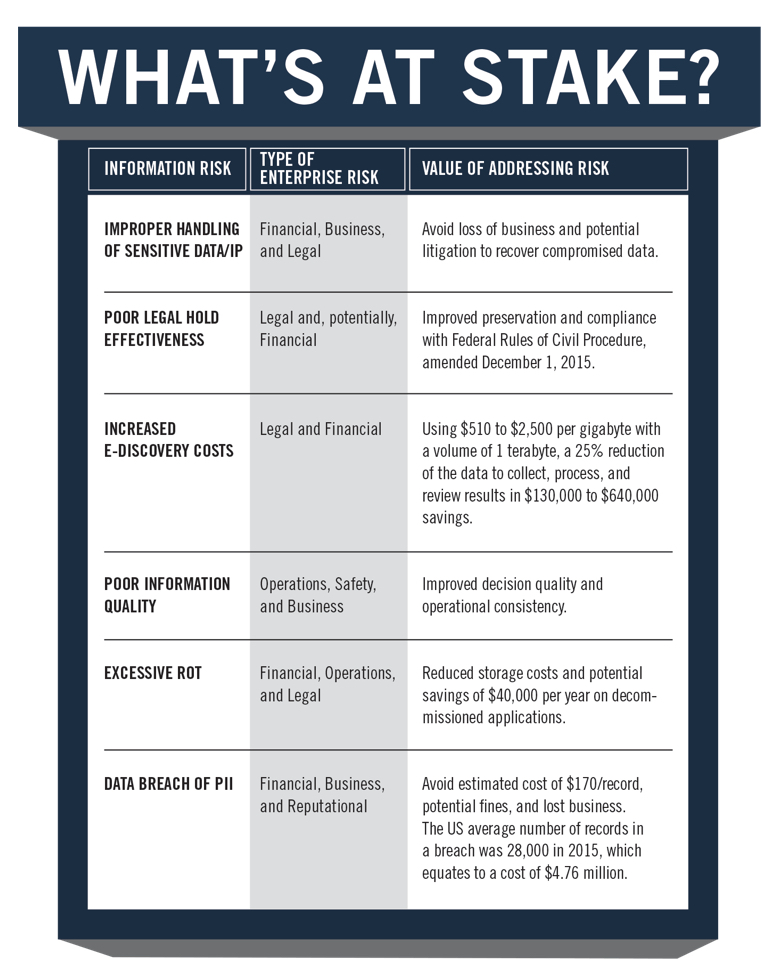
Employees are still to blame for many cyber incidents. Poor security awareness continues to be the greatest inhibitor to defending against cyber threats, followed closely by the massive volumes of data for IT security teams to analyze/protect. Cybersecurity professionals need to understand the information risks their organization faces and how to leverage information governance, along with technology, to get the biggest bang for their buck.
According to Gartner, some companies have spent $81.6 billion on security technology in 2016—and still experience data breaches. As a result, companies are turning to cyber insurance. Certainly, insurers will be happy for the additional business, but they won’t be handing out claim payouts easily. Insurers will investigate each breach thoroughly, and if negligence or the controls and cyber prevention technologies do not match what was represented in the insurance application, they will not pay on the claim. Many insurers will help their clients by developing programs that drive better security hygiene and by offering incentives for better detection and incident response capabilities. It makes one wonder if these programs or incentives will resemble what health insurance providers are dong. Will this be the cyber insurance equivalent to Fitbit?
So, what can be done? Cybersecurity professionals need to partner with information governance/information management professionals to jointly develop what Gartner calls a “data security governance plan.” This cross-functional team can work together to leverage technology that protects the enterprise yet enables business agility, to ensure information risk is reduced through a combined effort of governance and technology, and to effectively address the people and process part of the cyber security equation.
In a Gartner Special Report titled, “Cybersecurity at the Speed of Digital Business,” they call for the creation of a data risk officer. For this unique role to be filled effectively, organizations should cross-train their cybersecurity and information governance professionals. When cybersecurity technologists better understand governance and information risk and information governance practitioners better understand cybersecurity technologies, the more effective these two will be at protecting the organization.
Russell Stalters is the Founder of Clear Path Solutions Inc. and is a recognized information and data management expert. Don’t miss his session on the future of information security on Tuesday, May 2 at the DOCUMENT Strategy Forum in Chicago.












